Since cryptocurrencies and digital goods are a foundational part of the rapidly growing digital economy, crypto wallets are as important to Web3 as bank accounts are to Web2.
But with so many types of crypto wallets, it can be difficult to understand what they all do exactly and how to go about choosing one.
In this article, we answer many questions you may have around crypto wallets.
What is a crypto wallet?
A crypto wallet is a software program, a hardware device, or a piece of paper that securely stores the public and private keys pointing to a user’s cryptocurrencies on a blockchain.
Before going further, let’s quickly define what public and private keys are.
A “key” in the crypto space refers to an alphanumeric string. A key might look something like this: 0x839A957056D3a76f80A1AAfe7855B27d26c58301
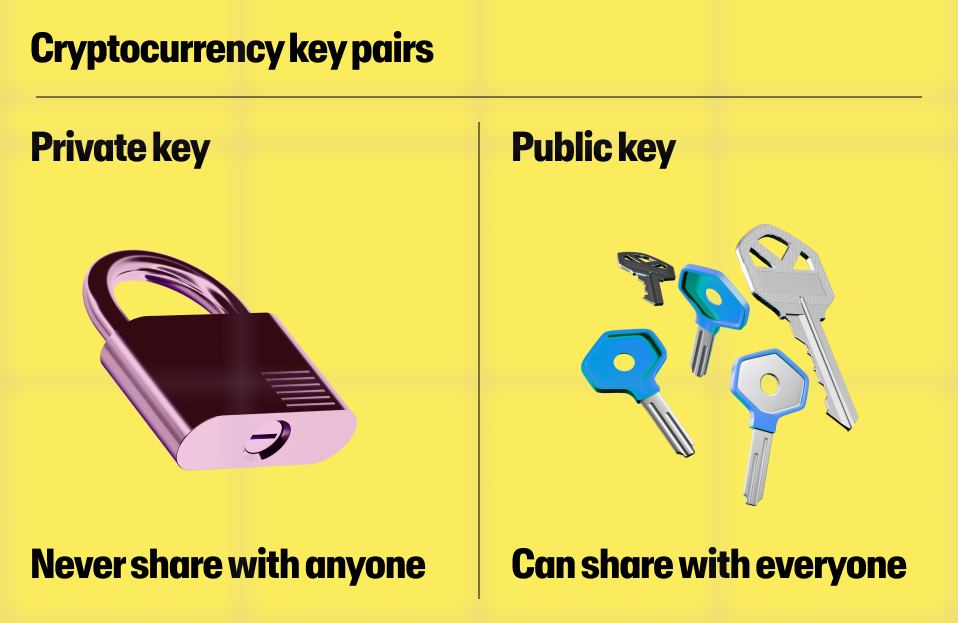
A public key is the crypto equivalent of a bank account number, which needs to be shared to allow others to make a transfer to you.
A private key, on the other hand, is more like a login ID and password to your internet banking, as they are used to access your assets—if you lose your private keys, you risk losing your assets.
In other words, you can share your public key with anyone who wants to transfer crypto assets to you, but you should never share your private keys.
Depending on how a crypto wallet stores a user’s private keys, wallets can be categorized under four broad categories: hot wallets, cold wallets, custodial wallets, and non-custodial wallets. These will be explained in more detail later in the article.
Why do you need a crypto wallet?
Web3 is huge, consisting of thousands of dApps and DeFi platforms hosted on various blockchains. Cryptocurrencies form a basic financial unit of this massive ecosystem.
Since crypto wallets store the keys that give users access to cryptocurrencies living on the blockchain, they form the base of all financial interactions in the Web3 space. Anyone who wants to connect with dApps or conduct a transaction on the blockchain needs a crypto wallet.
Crypto wallets provide a real-time record of the digital assets you own, and enable you to send, receive, trade, swap, or transfer them.
How do crypto wallets work?
Crypto wallets store the public and private keys associated with your crypto assets on the blockchain.
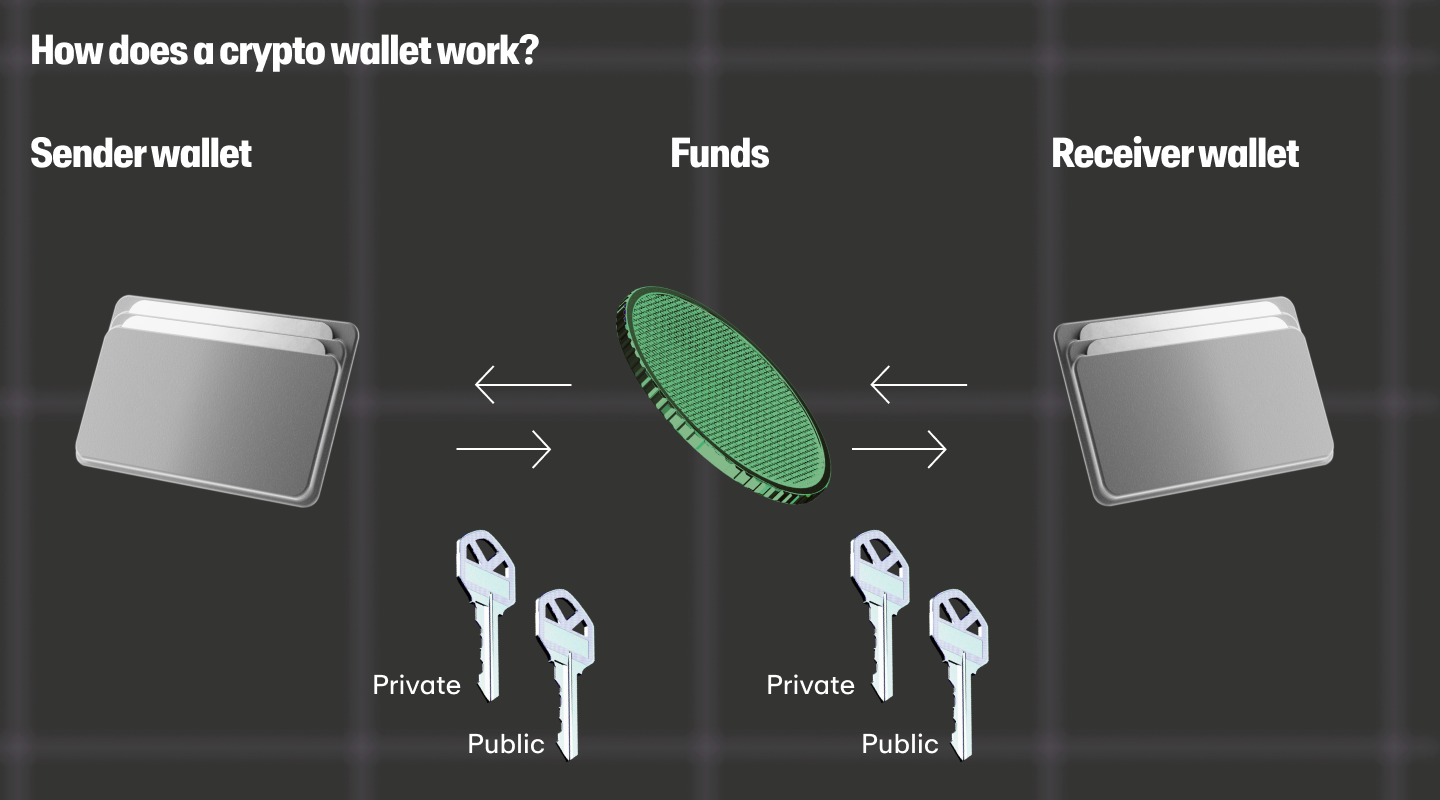
You can use these keys to connect to Web3 platforms or execute transactions that are broadcast to the blockchain. In the case of cryptocurrency transactions, the blockchain network validates the transaction before updating it on the network, which then reflects as the updated balance in your crypto wallet.
For instance, if A wants to transfer 10 BTC to B, A will require the public key of B’s wallet address. Once A confirms the transaction, it is sent to the blockchain and processed. A's wallet balance will then display 10 BTC less, while B’s wallet address will show 10 BTC more.
Hot wallets vs. cold wallets
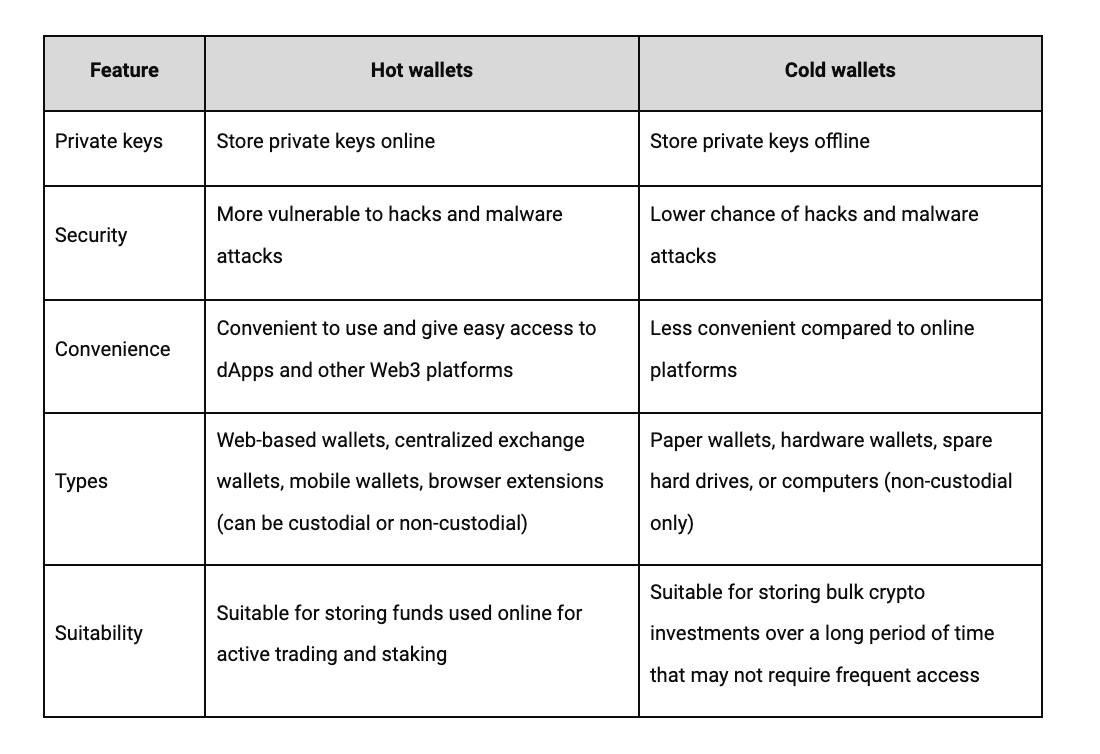
The first way to classify crypto wallets is to consider where a wallet stores the public and private keys. Based on that criterion, there are two types: hot wallets and cold wallets.

Hot wallets
A hot wallet is a crypto wallet that stores your private keys online and stays connected to the internet.
Hot wallets can come in the form of a browser-integrated extension, a mobile application, a desktop client, or a centralized exchange wallet.
Some examples of hot wallets include MetaMask, WalletConnect, Argent, Temple Wallet, and Coinbase.
Since hot wallets are connected to the internet, they make cryptocurrencies linked to them more accessible. This enables you to more easily connect your wallet to decentralized applications so you can explore what the Web3 ecosystem has to offer.
Cold wallets
Unlike hot wallets, cold wallets are crypto wallets that store your private keys offline.
Since your keys are stored offline, they are more guarded against hacks, theft, and system malware than hot wallets. If a hacker wanted to steal the crypto assets associated with your hardware wallet, they would still need to somehow attain physical possession of the wallet and associated passwords to access those crypto assets.
Cold wallets can come in the form of paper wallets, secondary offline computers, and hardware wallets. All these cold storage methods are secure. Some popular hardware cold wallets are the Ledger Nano S Plus and Trezor Model One.
Hot vs. cold wallets: which is better?
Hot wallets and cold wallets serve specific purposes, and both have their pros and cons. Different wallets may be more suitable for a particular use.
Custodial vs. non-custodial wallets
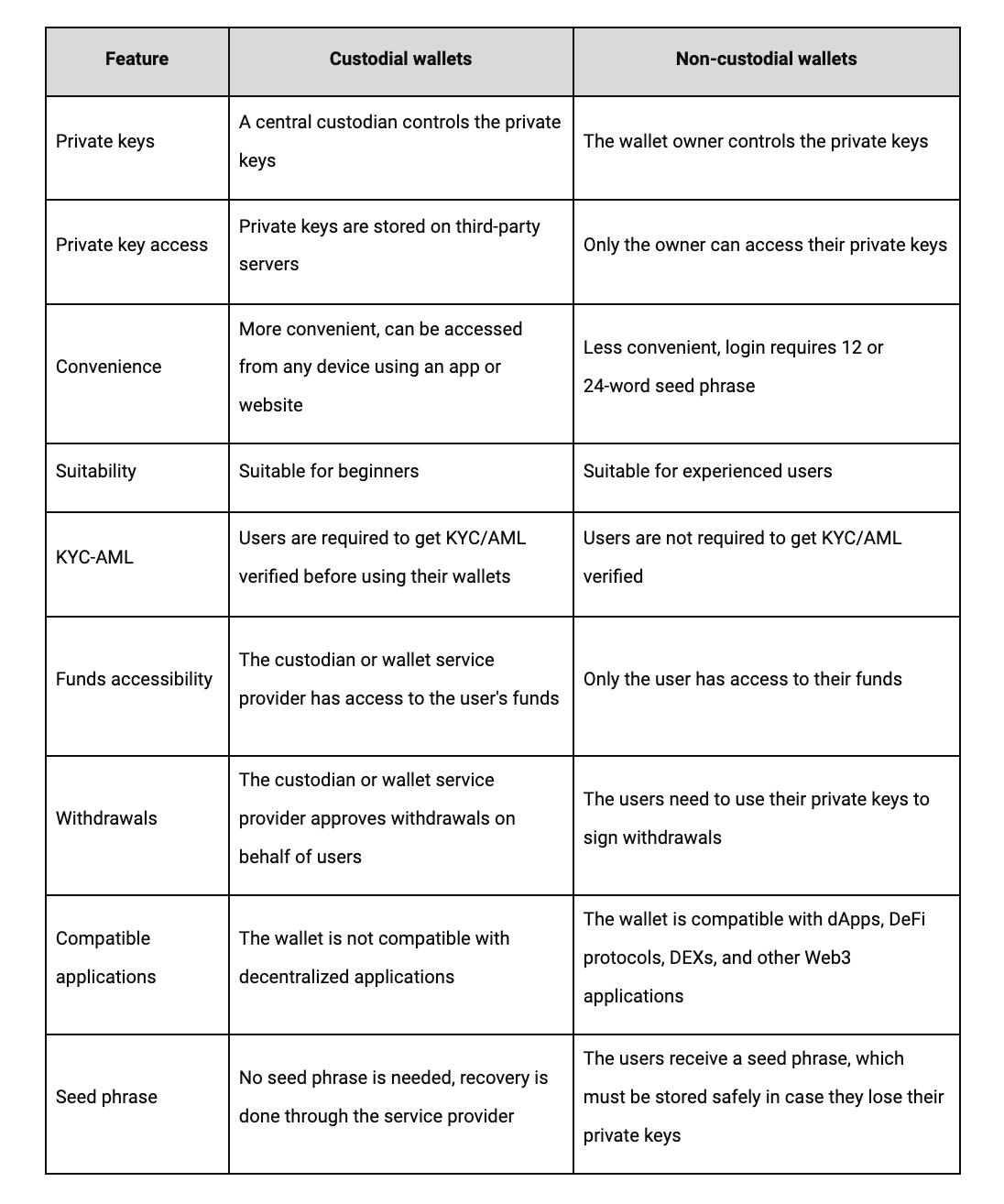
The second way to classify crypto wallets is to consider who stores and controls the private keys. Under this classification, there are two primary types of crypto wallets: custodial and non-custodial.

Custodial wallets
A custodial wallet is a wallet in which a third party is responsible for managing your private keys. Instead of having complete control of your private keys (and therefore your crypto assets accessed by those keys) the third party has control over your private keys (and therefore your crypto assets accessed by those keys).
The most popular examples of custodial wallets are those provided by crypto exchanges such as Coinbase, Binance, and Kraken.
One of the advantages of custodial wallets is that they act as an easy on-ramp for beginners in the crypto space. Additionally, they allow users to participate in staking and yield farming (the process of locking crypto assets in a protocol to earn a percentage payout) without the need to log into decentralized protocols.
Recommended reading: Yield farming vs staking
Non-custodial wallets
A non-custodial wallet is a wallet in which you are responsible for storing and managing your private keys. Instead of third parties having custodial access to your private keys, you have full control over your digital assets.
Non-custodial wallets exist in many forms, such as browser-based wallets like Brave, mobile applications like Argent, and hardware wallets like Ledger. You can use these wallets to log in to DeFi protocols and decentralized applications.
Custodial vs. non-custodial wallets: which is better?
Custodial and non-custodial wallets each have their own uses. How one weighs their advantages and disadvantages depends on what they want from a wallet.
Read our article Custodial vs. non-custodial wallets to learn more about how these wallet types differ.
What is a paper wallet?
A paper wallet is a piece of paper with cryptographic keys printed on it. The keys can be handwritten or printed as either plain text or in the form of a QR code.
Paper wallets leave no trace on the internet, ensuring crypto assets remain safe from online threats.
Although paper wallets are safer than hot wallets, they can easily get lost or destroyed. Currently paper wallets aren’t a popular choice given the variety of hardware wallets that serve the same purpose and are extremely durable and safe.
What is a hardware wallet?
A hardware wallet is a physical device, such as a USB or Bluetooth device, that stores your public and private keys. They are built to be safer from hacks and thefts.
Hardware wallet users can still use their funds across dApps by linking the wallet to an internet-connected device. Even when connected to the internet, most hardware wallets do not expose your private keys to the internet. Instead, they first sign transactions within the device and then broadcast them to the blockchain network.
Some hardware wallets even require users to physically push buttons to sign a transaction, adding another layer of security against virtual threats.
Crypto wallet security
Any time you engage with a wallet you must take adequate security measures to protect your assets from theft.
Here are two of the most important things to keep in mind to keep your crypto assets secure:
Keep your seed phrase safe
A seed phrase, or recovery phrase, is a set of 12 or 24 random words generated by a non-custodial crypto wallet when it is set up. The words are usually drawn from the BIP39 standard, a list of 2,048 English words and the most common standard used to generate seed phrases.
Your wallet’s seed phrase can be considered the most significant layer of wallet security available because it acts as an emergency backup if you ever lose your private keys.
Since the seed phrase plays such an important role in securing your assets, you must memorize it or write it down somewhere secure.
Store limited funds on crypto exchanges
Despite the many security measures exchanges take to protect user funds, they are still prone to hacks and thefts. Besides, there’s always a risk of a crypto exchange pausing withdrawals for several reasons, leaving users blocked from using their own funds.
Hence, users should only store a limited portion of their crypto assets on custodial wallets.
Which crypto wallet should you use?
Choosing a crypto wallet entirely depends on individual needs.
Here are a few things to consider when making a choice:
- The level of control you want over your funds
- Ease of use
- The number of coins a wallet supports
- The fees for using wallet services
- Which use cases you’ll need your funds for (e.g. dApps or DEXs)
- The security features offered by the wallet
- The user-friendliness, platform compatibility, and reputation of the platform hosting the wallet
The ideal setup would be to use a combination of both hot and cold wallets, keeping only small quantities of cryptocurrencies online at any given time.
Begin your crypto journey
Once you’ve chosen a crypto wallet, you can top up with MoonPay.
Simply buy Bitcoin or your preferred cryptocurrency via MoonPay using your credit card or any other payment method.
MoonPay also makes it easy to sell crypto when you decide it's time to cash out. Simply enter the amount of the token you'd like to sell and enter the details where you want to receive your funds.

.png?w=3840&q=90)




