If you want to buy your morning coffee with cryptocurrencies, beware that it may take anywhere from 15 seconds to a few minutes for the blockchain to process your transaction.
But why? Well, blockchain transactions are sometimes slow. Without scaling solutions, network congestion can cause delays and incur occasionally massive gas fees.
So, what are Layer-1 blockchains and how do their architecture limit their ability to process transactions quickly?
This article explains what Layer-1 blockchains are and explores innovations that are helping to make them faster and more cost-effective.
What is a Layer-1 blockchain?
A Layer-1 blockchain is the base level of the blockchain architecture. Layer-1 blockchains validate and execute transactions without support from another network, and reimburse transaction fees with cryptocurrencies.
For example, Ethereum runs transactions without depending on an external system and has its own native cryptocurrency, Ether (ETH). Solana is another Layer-1 blockchain, which was created to provide more efficient transactions with lower fees.
Layer-1 scaling solutions
Blockchains aren’t big on scalability. While centralized payment systems like Visa process at least 1700 Transactions Per Second (TPS), Bitcoin and Ethereum are capped at 4.6 and 15 TPS respectively.
So why are blockchain scaling solutions so difficult to implement?
Blockchains need to access the system’s entire database to verify a transaction and add a new block to the blockchain. This process is computationally (and sometimes environmentally) intensive, limiting processing speeds to just a few transactions per second.
Vitalik Buterin, the co-founder of Ethereum, was the first to define this problem, also known as the blockchain trilemma.
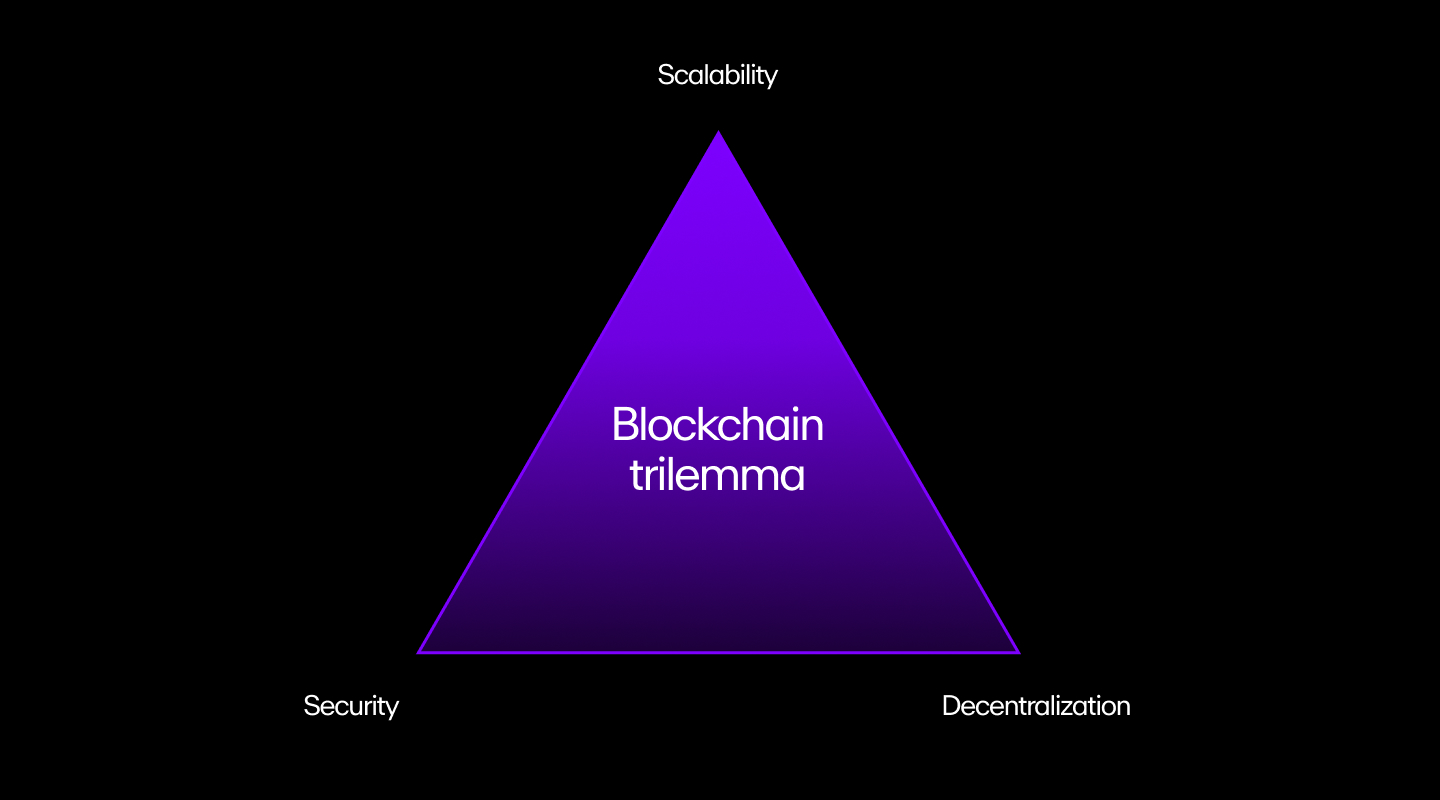
All blockchain networks need to have three properties:
- Decentralization: The chain runs without depending on centralized actors. In other words, no organization or government runs it, and a distributed network of computers (nodes) manages everything.
- Security: The chain can resist an attack from at least 51% of the participating nodes.
- Scalability: The chain can support an increasing load of transactions.
According to the trilemma, a blockchain can only have two of the three properties at a given time.
Different approaches to solve the blockchain trilemma
Since the blockchain trilemma was first introduced, numerous measures were proposed to address it.
Some measures like Segregated Witness (SegWit) are simple soft forks where only the code changes and users continue using the same blockchain.
But others like consensus mechanism changes may cause a hard fork that splits chains and impacts the value of certain cryptocurrencies.
In short, each method comes with intrinsic trade-offs, while attempting to improve scalability.
1) Change the consensus mechanism
In blockchain technology parlance, “consensus” is reached when a majority of the blocks agree on the state of the network. For example, if a blockchain network is processing a transaction, at least 51% of nodes should decide that it’s valid to execute it and add it as a block to the chain.
Theoretically, if hackers want to modify this transaction, they’ll have to attack 51% of the system to change the consensus.
Consensus mechanisms (also called a consensus algorithm or protocol) ensure that the “51% attack” doesn’t occur and compromise the system.
Bitcoin’s Proof of Work (PoW) mechanism is one of the most prominent examples of a consensus mechanism. Proof of Work is done by miners who compete against each other to solve complex puzzles and earn BTC by adding new transaction blocks to the blockchain.
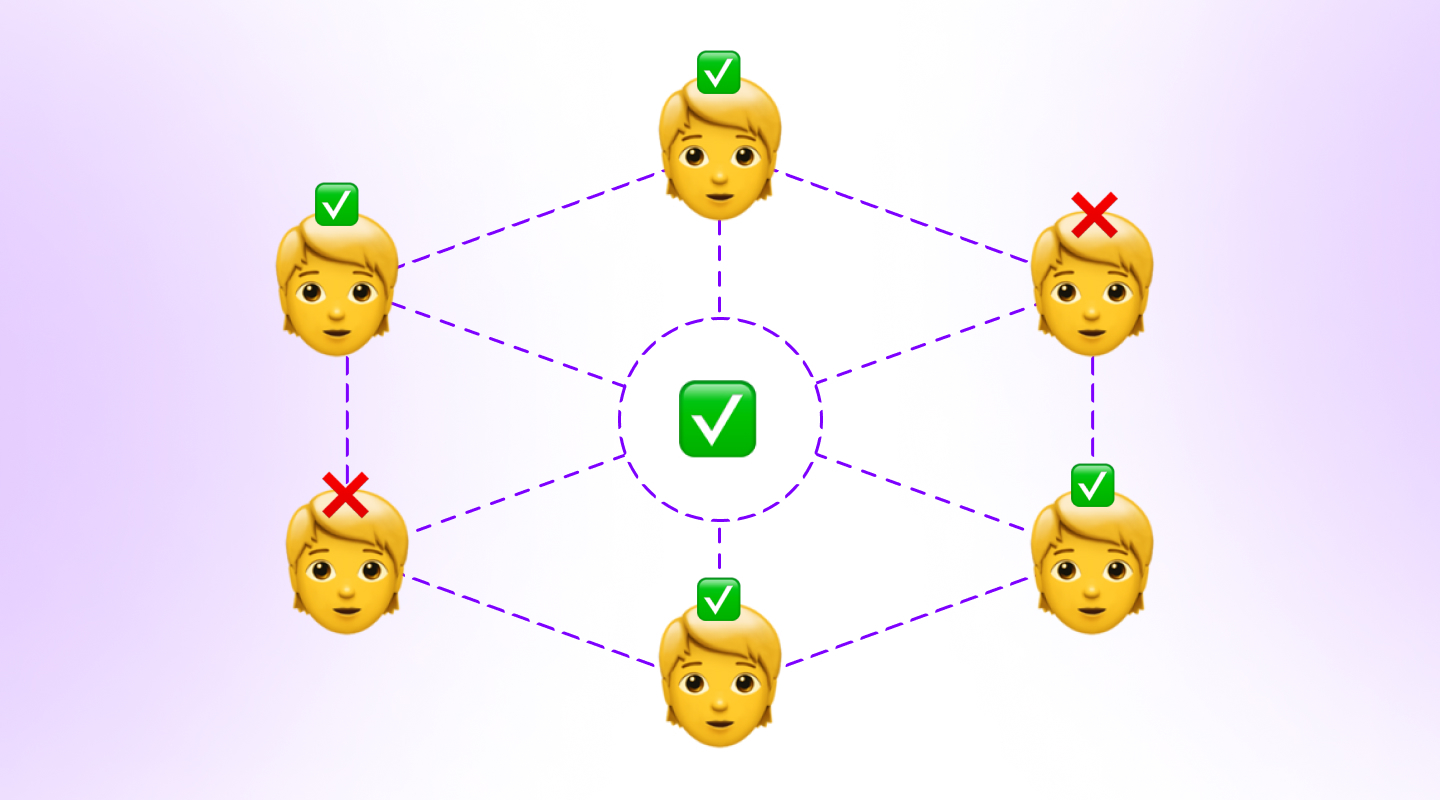
This mechanism is secure because it incentivizes users to contribute to the network to generate rewards, but it’s also computationally intensive and limits scalability. This is why Ethereum has opted to move to a Proof of Stake (PoS) model in which a validator is chosen randomly to create new blocks.
Such changes in consensus mechanisms can help enhance scalability, but it’s still not ideal as new consensus mechanisms take years of research to develop and may present different risks.
2) Increase the block size
Blockchain scaling solutions are necessary when the block isn’t large enough to process transactions. So naturally, increasing its size may seem like an obvious solution.
But contrary to what one might think, increasing the block size (B) won’t solve the problem as there are other crucial factors called relay time (TR) and block generation time (TB) involved in the process.
TR is the time needed to broadcast a new block to every node on the network, while TB is the time needed to generate a new block.
Let’s imagine B is hard-coded at 1 MB. If we double its size to 2MB, it would also increase the time each node takes to download the block, which doubles TR time and places a lower limit on TB.
Here’s a hypothetical example that uses the Bitcoin network:
As of January 2021, the Bitcoin network had about 10,000 nodes, and the average time it took to update 99% of the network about a new block, TR99, was about 14 seconds.
Increasing B would push this value to 28 seconds and limit TB to 28 seconds.
If the time taken to generate a block falls below this value, a new block will be generated before all the nodes in the system receive the previous block.
This could lead to critical security vulnerabilities like double-spend attacks, where the same currency is spent twice on different transactions as the user made another transaction before the network was updated.
Currently, the Bitcoin network’s TB is about 10 minutes, and bringing the TB to 28 seconds sounds like a win. But it still won’t be enough to match Visa’s 1,700 transactions per second.
3) Segregated Witness (SegWit)
Before understanding what SegWit is, let’s examine why it was implemented.
All transactions that take place on a blockchain platform have three components: the sender (input), the digital signature (authentication), and the receiver (output.)
The digital signature plays an essential role in these transactions as it ties a person’s identity to the transaction.
If you signed a cheque to transfer funds to another person, you can’t deny the transfer as your signature proves you authorized it.
Although this verification method looks foolproof, there’s also room for manipulation. For instance, the attacker can change the transaction ID slightly to create a new transaction.
Since the sender can’t find the original transaction on the blockchain, the attacker can ask the sender to resend funds and keep the funds from the original transaction.
These attacks are called transaction malleability, and a SegWit was initially implemented to address this issue.
By doing so, it also accidentally addressed the scalability issue by increasing the block size in the chain.
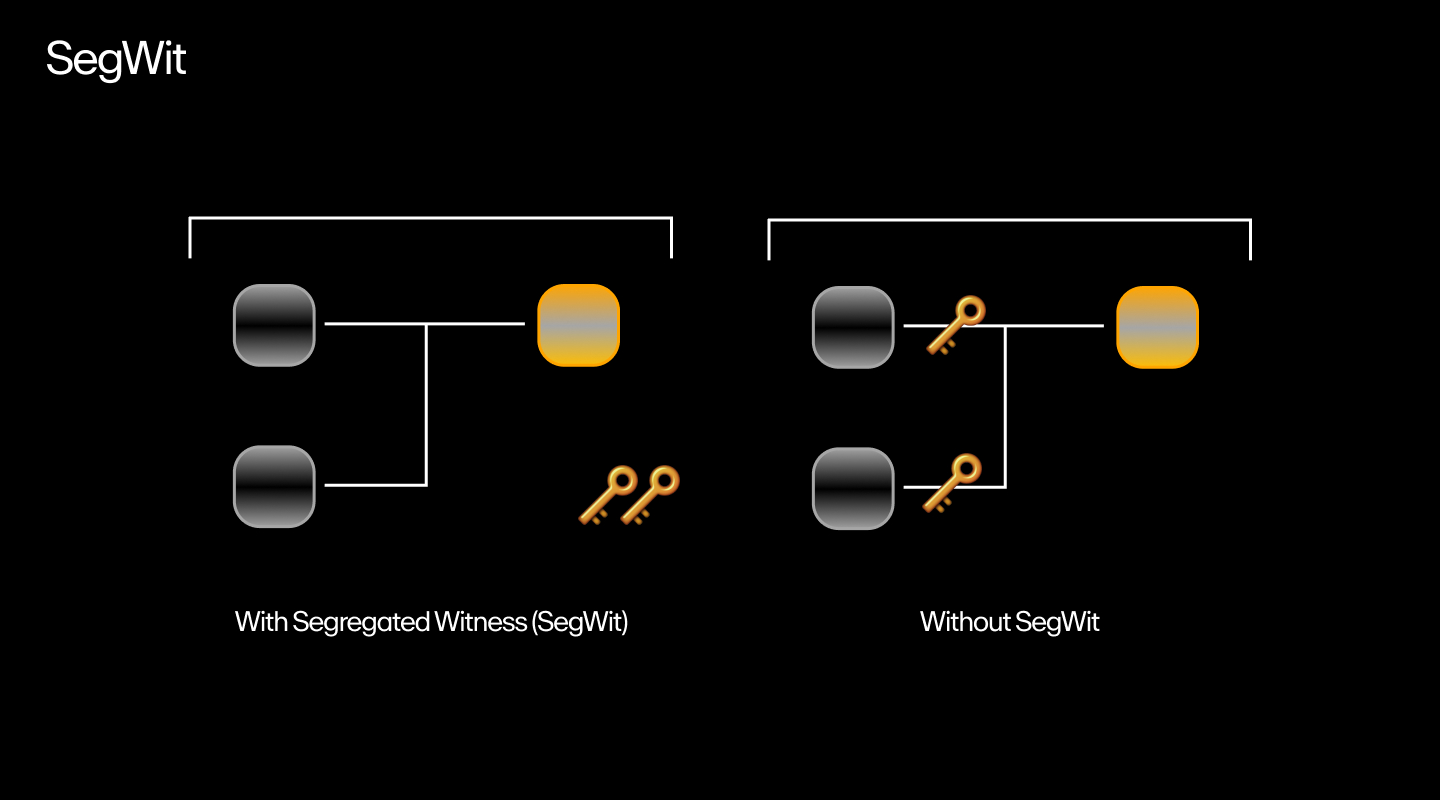
How SegWit works
SegWit is a network upgrade that aims to separate transaction signatures from the main block so the latter can process more transactions.
This means the system now has two blocks: the main block, or legacy block, and the SegWit block. These SegWit blocks move the digital signature and other “witness data” from the Legacy block and place them in an extended block.
Since the witness data takes up 65% of the transaction size, it frees up space for more transactions within the legacy block and improves TR. As a result, attackers can’t change the transaction ID before the nodes verify it.
The upgrade also improves the TPS, but the increase isn’t enough to solve the scalability issue. This is where a more efficient scaling solution called sharding comes in.
What is Layer-1 sharding?
Layer-1 sharding splits a network into subsets called shards and assigns a set of transactions to each. This way, the system processes multiple transactions simultaneously instead of a single transaction.
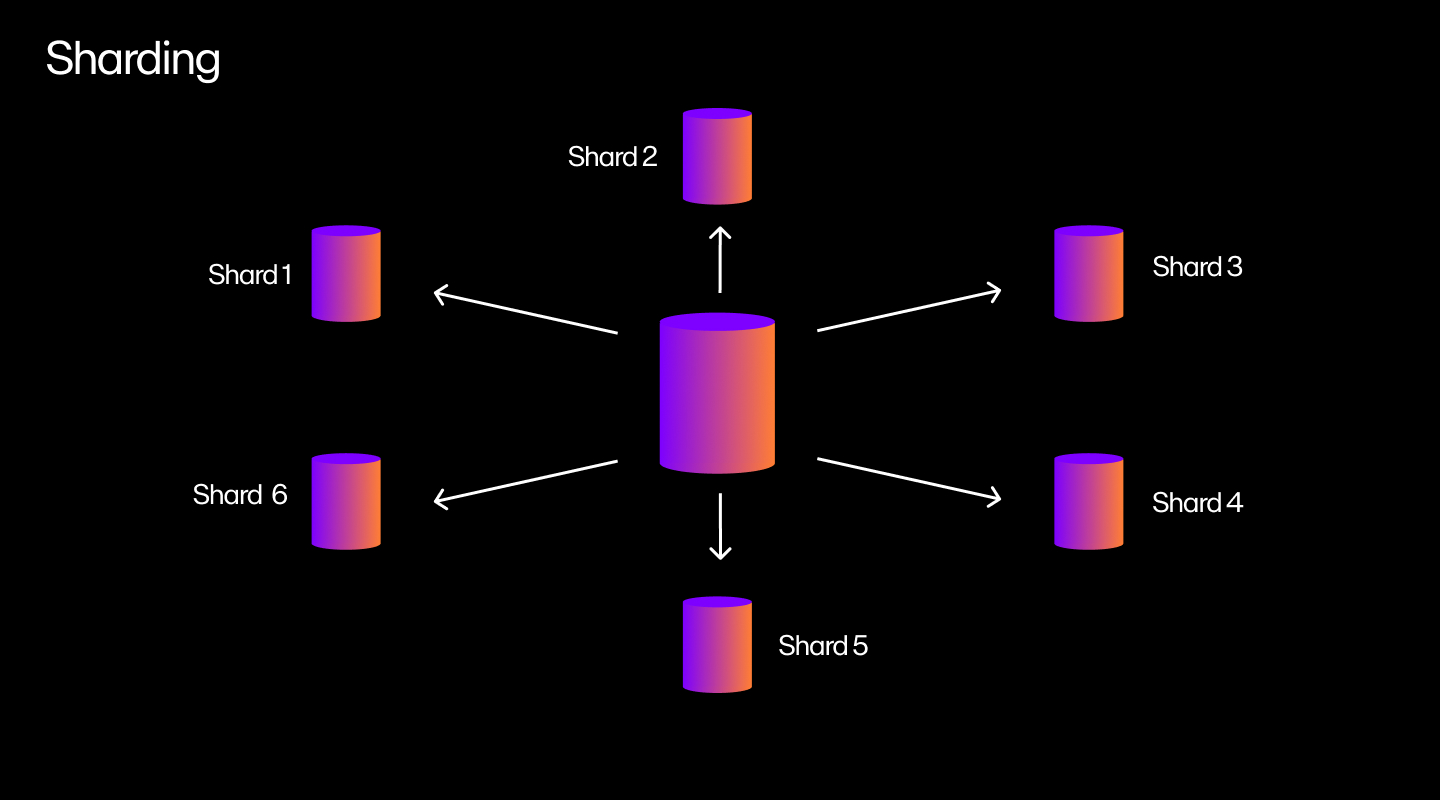
Suppose you have a network of 10,000 nodes and 100 blocks to verify. The network randomly assigns the first 100 nodes to verify the first block, the second 100 nodes to verify the second block, and so on.
When validators verify a block, they publish a signature attesting to the verification. Now, the remaining nodes only validate the 10,000 signatures, which takes less time than verifying the blocks.
Does sharding have the same security issues as a multi-chain ecosystem?
Sharding is more secure than a multi-chain ecosystem (a system with several interconnected blockchains) but less secure than a Layer-1 blockchain.
In a multi-chain ecosystem, an attacker can wreak havoc even if they get control of 0.5% of the total stake (total assets locked in the system).
But with sharding, the attacker would have to get at least 30-40% of the stake to attack the system. Given the random sampling method it employs, it becomes very difficult for a hacker to concentrate their power on a single shard.
Furthermore, if a shard produces a bad block, the system throws it out and the entire chain reorganizes itself to avoid it.
For instance, suppose there are two smart contracts, A and B, and contract B misbehaves. The network will revert the transaction. Thus, sharding provides better security than multi-chain ecosystems (but less security than a Layer-1 blockchain) and is scalable.
Layer-1 vs. Layer-2 blockchains
As we saw earlier, Layer-1 solutions must make compromises to security to significantly improve scalability.
This is where Layer-2 solutions come in.
These frameworks allow transactions to be processed off-chain (chains outside the main chain) so that the main chain only receives a summary of what’s been completed.
Although this slight modification doesn’t sound like much, it significantly reduces the load on the blockchain, thereby improving its scalability and gas fees.
Bitcoin Lightning Network
The Lightning Network (LN) is a separate peer-to-peer (P2P) network built atop the Bitcoin blockchain. It has two functions:
- Monitor the blockchain.
- Interact with other lightning nodes to transfer money.
The LN only communicates the opening and closing transactions to the main chain. Intermediate transactions between two parties are stored in a private ledger.
For example, if Alice and Bob enter into a contract to transfer 5 BTC to Bob in five transactions of 1 BTC, the Lightning Network will only show the final state of the blockchain.
In other words, the records will only show the 5 BTC that Bob received in the end instead of showing the five transactions.
The best part is that the Lightning Network doesn’t incur any gas fees unless you route payments through multiple parties. This also allows for smaller transactions or micropayments as low as 0.00000001 BTC.
Layer-1 blockchain examples
Layer-1 blockchains aren’t just limited to Bitcoin and Ethereum. They include other blockchains that support many unique use cases.
MultiversX (Elrond)
MultiversX (formerly Elrond) is designed to compete against big players like Ethereum and Bitcoin by improving scalability and reducing computational waste. Its unique feature is its adaptive state sharding mechanism which improves scalability by combining three types of sharding:
- Network sharding: Handles how nodes are grouped into shards.
- Transaction sharding: Maps transactions to the shards.
- State sharding: Shards only have a partial view of the state, incorporating cross-shard communication during transactions.
BNB Chain

The BNB chain includes the initial Binance Chain launched in 2019 and its upgraded version, the Binance Smart Chain , which was introduced in 2020.
When Binance launched in 2019, its primary focus was to replace the poor user interface of decentralized exchanges (DEXs) with an ultra-fast and decentralized trading option.
After a year's successful stint, the Binance Chain launched the Binance Smart Chain to compete with Ethereum and its functionality to host decentralized applications (dApps).
The Binance Smart Chain runs in parallel with the Binance Chain and relies on Proof of Stake consensus where participants can be become validators by staking Binance Coin (BNB). BSC is also compatible with the Ethereum network, allowing developers to migrate dApps with minimal difficulties.
Solana

Solana is touted as the first web-scale blockchain network that supports transaction speeds of up to 65,000 TPS with 200 nodes under testnet conditions (a testnet is an alternate blockchain used for testing).
Its core innovation is the Proof of History (PoH) mechanism that combines elements of Proof of Stake. While other blockchains rely on other nodes to verify if a transaction occurred, Solana uses cryptographic timestamps to establish the order of events.
You can think of this as adding a few drops of dye to water in a container and taking a picture at fixed intervals. If the photographs were scrambled, you’d know how to rearrange these pictures as they’re a function of time.
Each node in Solana has a clock that allows the network to reach consensus on the time and order of events without waiting for confirmation from other nodes. The nodes can therefore validate transactions without relying on other nodes, which reduces network congestion and improves scalability.
THORChain

Although DEXs have become more popular lately, it’s still not possible to trade tokens across different blockchains. For example, Bitcoiners can’t trade BTC on Ethereum, Ethereans can only trade ERC-20 tokens on Ethereum’s DEXs, and DEXs on Solana only support SOL tokens.
Enter THORchain.
THORchain is a cross-chain DEX that allows you to trade one digital asset with another digital asset on a separate chain, similar to DEXs like Uniswap.
However, in addition to liquidity providers who deposit their tokens in pools, the THORchain has another component called THORNodes (servers or cluster of servers.) These THORNodes consist of a THORChain node and a node for each supported chain.
For example, if a user wants to swap ETH for BTC, the Ethereum nodes will detect and agree the ETH vault has received the ETH. Then, these nodes collectively sign the BTC transaction from the Bitcoin nodes to make the exchange.
Kava

Kava features a unique co-chain architecture that combines the interoperability of Cosmos SDK and the flexibility and speed of Ethereum smart contracts.
The result is a highly scalable and secure blockchain that connects to the 30 chains in the Cosmos ecosystem and an Ethereum-compatible environment that empowers developers to deploy apps on Cosmos and Ethereum.
Also, all transactions are ultra-fast and secure as they’re powered by the Tendermint consensus engine and its ability to achieve block finality which guarantees that a transaction can’t be altered.
Closing thoughts on Layer-1 blockchains
The blockchain ecosystem has developed several Layer-1 and Layer-2 solutions to deal with the blockchain trilemma. Most Layer-1 scaling solutions negatively impact blockchains by upsetting the balance between the other two factors, decentralization and security.
Layer-2 solutions, however, build atop an existing Layer-1 solution to improve its scalability while also retaining decentralization and security.
But while Layer-2 solutions may be seen as better in this regard, that doesn’t mean Layer-1 blockchains are obsolete. There are many promising Layer-1s that have solved scalability efficiently and made great strides in decentralized finance (DeFi).
Get started with Layer-1 blockchains
Now that you have a better understanding of Layer-1 blockchains, you might want to explore them for yourself.
To get started, simply buy Bitcoin, Ethereum, and many other L1 cryptocurrencies via MoonPay using a credit card or your preferred payment method.
MoonPay also makes it easy to sell crypto when you decide it's time to cash out. Simply enter the amount of the token you'd like to sell and enter the details where you want to receive your funds.




.png?w=3840&q=90)

.png?w=3840&q=90)