When it comes to digital security, encryption is key (pun intended).
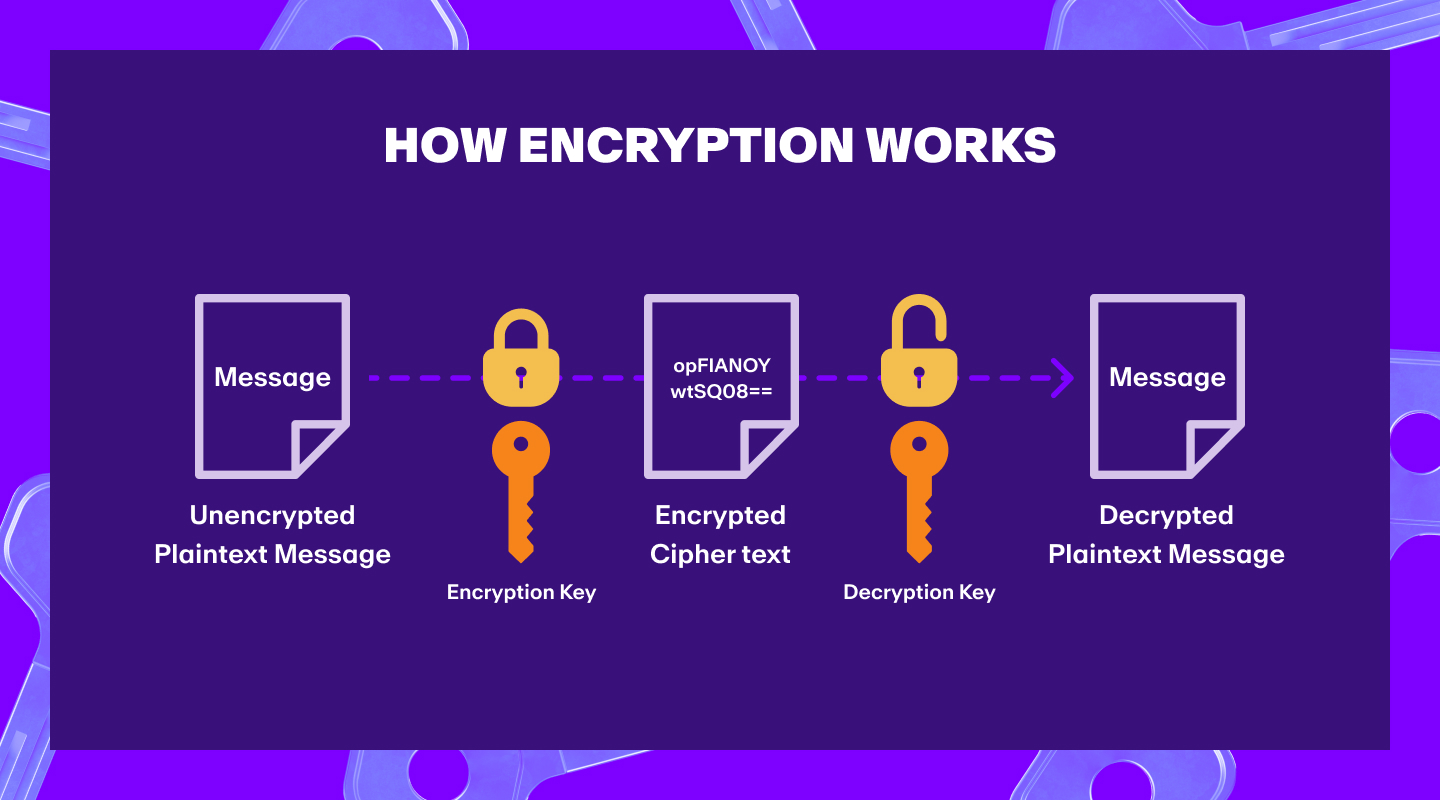
Encryption converts data into complicated code that can only be decoded with a specific “key”, making it possible to keep digital data secure without the need for a central authority.
This concept is called cryptography and, as you can probably guess, it’s at the core of cryptocurrency and Web3.
In this article, we’ll take a closer look at cryptography basics and the kinds of keys used to decode data.
What Is Cryptography?
Cryptography is the practice of encrypting data in order to securely communicate information between parties. It involves creating written or generated codes that allow information to be kept secret, and only accessible to someone who possesses the key to decode it.
The more complicated definition of cryptography is that it’s the study of mathematical techniques related to aspects of information security, such as data confidentiality, data integrity, entity authentication, and data non-repudiation.
Typically, data is encrypted in two ways:
- Symmetric encryption: the same key is used to encrypt and decrypt data.
- Asymmetric encryption: two different keys are used to encrypt and decrypt data. One key is used to encrypt and another is used to decrypt.
Did you know? Most cryptocurrencies use asymmetric encryption, with a private-public key pair (we’ll explain what this is shortly) to read and write transactions on the blockchain.
What Is a Public Key?
A public key is a cryptographic code that allows users to receive encrypted messages and verify digital signatures. In the realm of Web3, it is also known as "public address" and functions as a cryptographic key used to receive cryptocurrency.
You can think of a public key as similar to your bank account number, which people use to send you money.
A public key is mathematically derived from a corresponding private key, and it is safe to share with others. In fact, you need to share your public key if you want people to send you cryptocurrency.
What Is a Private Key?
A private key is secret cryptographic code used to decrypt messages encrypted with a corresponding public key or to sign digital messages and transactions. In crypto, it is sometimes called a "secret key" and functions as a cryptographic key used to sign cryptocurrency transactions.
You can think of a private key as similar to your bank PIN number, which you use to access your bank account.
Your private key should never be shared with anyone, as it’s the only way to access your crypto assets. If you lose your private key, you are likely to lose your assets too.
How Are Public and Private Keys Related?
As mentioned earlier, a public key is mathematically derived from a private key.
More specifically, a public key is the result of applying a one-way mathematical function to a private key. This function is designed in a way that makes it very difficult, if not impossible, to determine the private key with just the public key.

This is called a private-public key pair. It’s how you can share your public key with anyone, and they can use it to send you cryptocurrency, but they can’t use it to find out your private key and access your wallet.
It’s this encryption mechanism that makes cryptocurrencies secure. Even if someone were to hack into your computer, they couldn’t access your cryptocurrency without your private key.
Public Key vs Private Key: What’s the Difference?
A public key is like your bank account number, in that it's safe to share and used to receive funds. A private key is like your PIN, since it must be kept secret and is required to access or spend those funds. Together, they form a cryptographic key pair that secures transactions in cryptocurrency and digital communication.
While public and private keys are related, they aren’t the same. Here’s a quick run through of their main differences.
- A public key is generated from a private key through a one-way mathematical function, so it’s almost impossible to reverse the process and get the private key from the public key.
- A public key can be shared with anyone, whereas a private key must be kept secret.
- A public key is used to receive cryptocurrency, whereas a private key is used to sign transactions and send cryptocurrency.
- A public key is like a bank account number, whereas a private key is like a PIN number or password.
- Your private key should never be shared with anyone, as it’s the only way to access your cryptocurrency.
- If you lose your private key, you may lose your cryptocurrency. But if you lose your public key, it can be retrieved from the blockchain's ledger.
- Public keys are usually generated by a software wallet, whereas private keys are usually generated by the user like a password to a secret message.
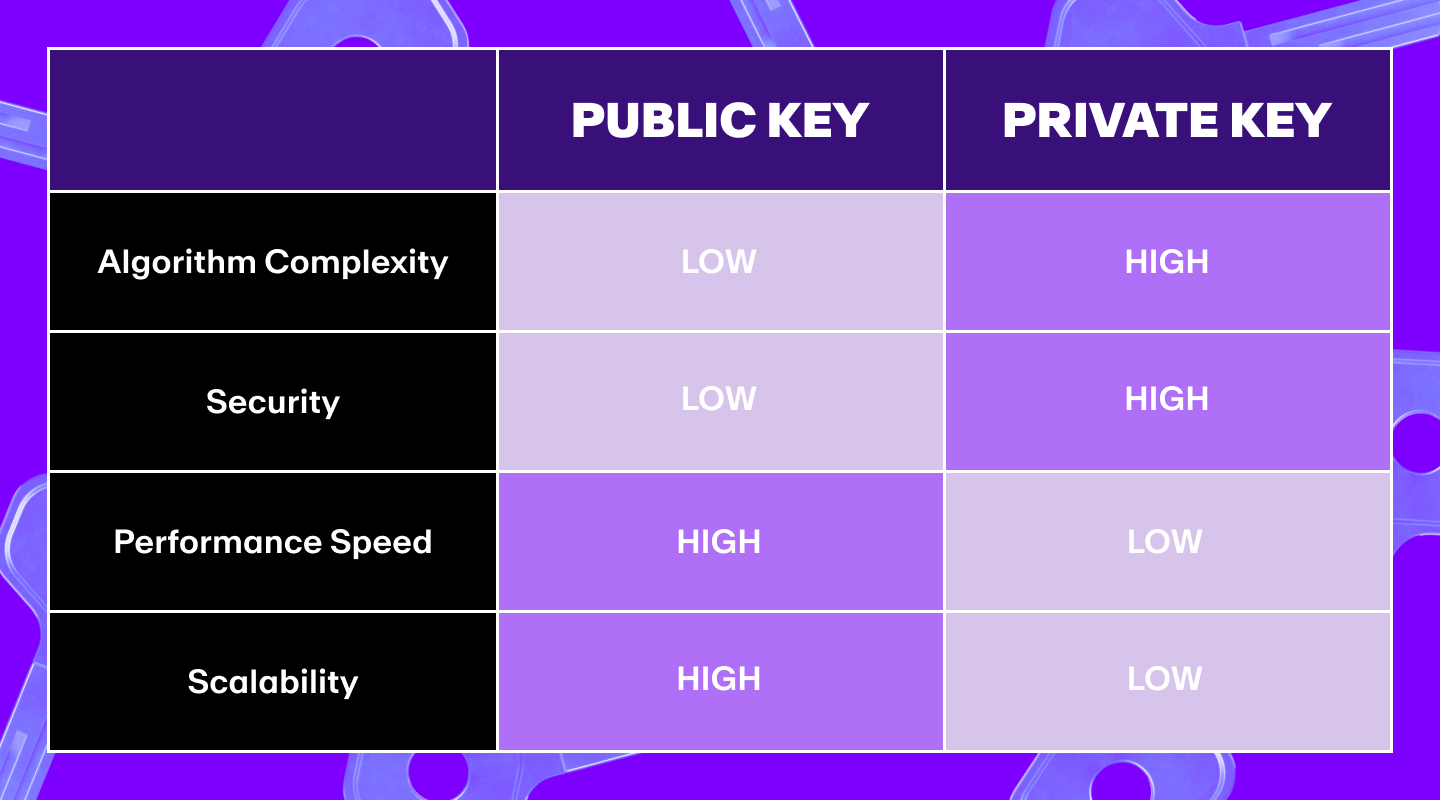
We can also use a table to illustrate some of the main public and private key differences:
Feature | Public Key | Private Key |
Purpose | Receive funds, verify signatures | Sign transactions, access funds |
Visibility | Shareable with anyone | Must remain secret |
Analogy | Bank account number | Bank PIN or password |
Generation | Derived from private key | Created first, source of the pair |
Loss Impact | Can be retrieved | Funds become inaccessible |
Benefits of Public Key Encryption
The main benefit of private-public key encryption is that it allows people to communicate securely, even if they have never met before.
For example, imagine that Alice wants to send Bob some cryptocurrency. If they were using symmetric encryption, Alice would need to know Bob's cryptographic key in order to encrypt the transaction.

If they are using asymmetric encryption, though, then Alice can simply look up Bob's public key on the blockchain and use that to encrypt the transaction. Bob would then use his corresponding private key to decrypt the transaction.
Similarly, if Alice wanted to send Bob a message, she could again look up his public key and use that to encrypt the message, and Bob can decrypt it with his private key.
Because it’s almost impossible to derive a private key from a public key, only the person with the corresponding private key can decrypt messages or transactions that are encrypted with the public key – and that’s why the system works.
So, private-public key encryption ensures:
- Confidentiality: only the intended recipient can decrypt.
- Authenticity: digital signatures verify sender identity.
- Integrity: tampered messages break the encryption.
- Open communication: secure even between strangers.
Drawbacks of Public Key Encryption
There are however a few challenges of public key encryption to consider.
Longer time to compute
The main disadvantage of private-public key encryption is that it can be slow and resource-intensive.
This is because the algorithms used for private-public key encryption are much more complex than those used for symmetric encryption. As a result, they can take longer to compute, and require more processing power.
Cipher text is expanded
The cipher text (the encrypted message or transaction) from public key cryptography can be significantly larger than the original plain text.
This is because public keys are typically much longer than private keys, and they need to be included in every encrypted message or transaction.
This can be a problem for cryptocurrency networks, which can struggle to handle large volumes of traffic.
Not suitable for large data sets
Another disadvantage of private-public key encryption is that it isn’t well suited for encrypting large data sets.
This is because the public and private keys are usually generated together, meaning they are the same size. If you want to encrypt a large data set, you’d need a much larger key.
This is why many cryptocurrencies use a hybrid system that combines private-public key encryption with symmetric encryption and hashing algorithms.
What Is Hybrid Encryption?
Hybrid encryption is a technique that combines both symmetric and asymmetric encryption. It’s typically used when speed and efficiency are important, but security is also a priority.
E-commerce websites are good examples of this—they need to encrypt large amounts of data, but should also be fast and responsive.
But how does it work? Well, a small amount of data is first encrypted with a public key. This is known as the "session key".
The session key is then used to encrypt the rest of the data using symmetric encryption. The session key is also encrypted with a public key, so that it can only be decrypted by the corresponding private key.
This system is much faster than public-private key encryption, while still offering quality security.
The downside, though, is that if the session key is compromised, the rest of the data can be decrypted—so keeping the session key completely secure is extremely important.
Hashing Algorithms and Hybrid Encryption
If a session key has to be a small piece of data, how do you make sure it’s the right size?
Hash algorithms.
A hash algorithm is a mathematical function that takes an input of any size and produces an output of a fixed size. The output is known as a "hash" or "digest".
Hashing algorithms are often used to store passwords because they can take any size input and produce a fixed-size output. This means that the password can be stored in a database without taking up too much space.
Hash algorithms are used in cryptocurrency wallets to generate wallet addresses.
There are lots of different types of hashing algorithms. Bitcoin, for example, uses the SHA-256 hashing algorithm.
When you want to send Bitcoin to someone, you'll need their wallet address. However, to save the impracticality of typing out a long and complicated address, you can use a hash of it. This is called a “Bitcoin address” or “address hash”.
Most Bitcoin wallets further simplify this for users by allowing them to copy and paste the wallet address when sending or receiving cryptocurrency.
Real-World Applications of Public Key Encryption
You may not know it, but you interact with private-public key encryption several times a day. It’s a system used across a wide variety of applications. Here’s just a few of them.
Digital signatures
Digital signatures are a way of proving that a piece of data has come from a specific person or entity. They are commonly used to protect the authenticity of documents, such as contracts.
A digital signature is created by combining the data with a private key. This produces a "signature" that can be verified using the corresponding public key.
If the digital signature is valid, this proves that the data came from the owner of the private key.
Secure Sockets Layer (SSL) / Transport Layer Security (TLS)
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are protocols that are used to encrypt data that is being transmitted over the internet.
They are commonly used on websites to protect user data, such as login details and credit card information.
When you see a website that has "https://" in the URL, this means it is using SSL/TLS.
Email encryption
Email encryption is a way of protecting the privacy of your emails. It works by encrypting the contents of your email with a public key so that only the intended recipient can decrypt it using their private key.
Secure Socket Shell (SSH)
SSH (Secure Socket Shell) is a protocol that is used to connect to remote servers. It uses public-private key encryption to authenticate users and encrypt data that is being transmitted.
Virtual Private Networks (VPNs)
VPNs (Virtual Private Networks) are used to encrypt data that is being transmitted over the internet. They are commonly used by businesses to protect sensitive data, such as customer information and confidential documents.
Private and Public Keys FAQs
What is the difference between a public key and a private key?
A public key is a cryptographic code that allows users to receive cryptocurrency and verify digital signatures. It can be shared openly.
A private key is a secret cryptographic code that allows users to sign transactions and access their cryptocurrency. It must be kept confidential.
Why is a private key important in cryptocurrency?
A private key is essential because it is used to sign transactions and prove ownership of the cryptocurrency. Without the private key, the user cannot access or transfer their crypto funds.
Can someone steal my cryptocurrency with just my public key?
No, a public key alone cannot be used to steal cryptocurrency. The public key is used to receive funds and verify signatures, but only the private key can authorize the spending of funds.
How is a public key generated?
A public key is generated from the private key using a cryptographic algorithm. This process is one-way, meaning the private key cannot be easily derived from the public key.
What happens if I lose my private key?
If you lose your private key, you lose access to your cryptocurrency. There is no way to recover the private key or the funds it controls, making it of utmost importance to store private keys securely.
Can I change my public key or private key?
You cannot change a public or private key once they are created, but you can generate a new key pair. However, any cryptocurrency sent to the old public key address will still require the corresponding old private key to access.
How should I store my private key?
Private keys should be stored securely, often in hardware wallets, paper wallets, or encrypted digital storage. It’s important to keep them offline and away from potential hackers.
You should never take screenshots of your private keys or store them anywhere online.
What is a key pair in cryptocurrency?
A key pair consists of a public key and a private key that are mathematically linked. The public key is used to receive funds, while the private key is used to sign transactions and access the funds.
Can my public key be used to determine my private key?
No, public keys cannot be used to determine private keys. The relationship between the keys is secure due to the cryptographic algorithms used, making it computationally impossible to reverse-engineer the private key from the public key.
Is it safe to share my public key?
Yes, it is safe and necessary to share your public key to receive cryptocurrency. However, your private key should never be shared with anyone.
Start Your Crypto Journey With MoonPay
Now that you know how public and private keys secure your crypto, it’s time to experience it for yourself.
With MoonPay, you can:
- Buy Bitcoin, Ethereum, and more with a card or bank transfer
- Top up your wallet in your local currency
- Enjoy quick processing, lower fees, and high approval rates
- Cash out securely to your bank when you’re ready


.png?w=3840&q=90)



